Back to Blog
Back to Basics: Digital Fraud
You have a 1 in 1,000,000* chance of being struck by lighting. A 1 in 3,800,000* chance of being killed by a shark. And a 1 in 292,000,000* chance of winning the lottery. Alas, if only those were the same odds as becoming a victim of digital fraud! Contrary to popular belief, identity theft statistics show that the chances of being a victim of fraud are much higher than you think. In post three of our Back to Basics series, we discuss the history of fraud, what types of fraud are on the rise, and how the industry is looking to manage it in the years ahead.
An Overview
Beginning in the 1990s, under the combined pressure of the EU’s expanding membership and its evolving single market, economic crime and corruption evolved into a pressing issue that, before then, never was seriously considered. As fraud continued to grow and develop well into the 2000s and until today, the need to protect the EU against financial crime has become an issue of high priority.
Financial fraud occurs when money or other monetary-based assets are stolen through deception or criminal activity. In the world of payments, the most common and severe outcome is identity theft, and there are two different ways that identity theft happens. One way is where they actually steal the identity. Another is by piggy-backing off an already established identity (e.g. malware doing a transaction in your banking app after you’ve authenticated yourself). Okay protects both types, but we focus primarily on the malware side as our expertise lies within the digital payments world. Nevertheless, fraud - in any form - undermines democracy, eats away at public trust, and puts an additional financial burden on governments (anywhere between 179-990 billion euros per year for the EU alone).
However, in today’s digital payments and post-data-breach world, fraud and risk prevention have become increasingly complex, mainly since the evolution of card-less payment fraud has gained momentum. No merchant, payment service provider, or bank single-handedly has all the data needed to determine if the customer or a fraudster has made a purchase. However, they do come close when their data is combined. The challenge then becomes finding a way to exchange this data quickly and safely so that the customer has little to no friction during their online purchases yet can be verified. The good news is that just as fraudsters and cyber criminals learn, improve, and innovate, so are payment service providers and their supporting processors, such as Okay.
The Rise of Digital Fraud
Many things are currently contributing to the rising fraud rates, including the growth of e-commerce and different forms of digital payments, not to mention fewer possibilities for customer verification due to cross-border trade. GDPR and Strong Customer Authentication (SCA) are other factors that help prevent yet complicate the world of fraud prevention because they make for ever-changing environments. This makes the traits of agility, creativity, and adaptability necessary for keeping up with fraudsters.
As we watch online payment transactions increase in number, we also watch forms of potentially fraudulent activities increase. Here are some stats (provided by Research and Markets via PRNewswire, in the European Online Payment Fraud and Security in 2022 report):
- B2C e-commerce economic losses due to online payment fraud were expected to increase by over 10% worldwide in 2021.
- Card fraud in e-commerce makes up more than 60% of all card fraud in the UK.
- Losses incurred from online payment fraud are projected to double worldwide in the five years between 2018 and 2023.
- In Germany, two-thirds of e-commerce companies have identified a noticeable rise in fraudulent activities.
- Over 85% of online retailers in Switzerland reported being victims of fraud.
Such trends push consumers to alter their payment habits in search of greater security. And in a parallel fashion, many institutions implement increased online security precautions to address consumer concerns.
As we mentioned in our last Back to Basics post, a huge reason PSD2 pushed SCA as a hard requirement was the debate around screen-scraping for initiating payments and the growth in unauthorised card fraud. In a 2021 report released by UK Finance called “Fraud the Facts”, they relay much of modern fraud to online vulnerabilities. This has been particularly true ever since the Covid-19 pandemic, when social distancing restrictions led to a significant increase in online spending and internet usage, providing better opportunities for cybercriminals.
While PSD1 was all about protecting us, as consumers, introducing One Time Passwords (OTPs) via SMS, PSD2 considers that fraudsters will up their games in a more digitised and sophisticated world ruled by mobile malware.
Common Types of Fraud
Criminals use a wide range of methods to commit fraud both directly and indirectly and have a collection of sophisticated fraud types, threats, and bots at their disposal. Card-not-present (CNP) fraud, which covers mainly “online fraud”, has become the most prominent type of card fraud. For many, card-related fraud is one of the most fascinating aspects of the payments industry because it is constantly changing. The graphic below highlights the emerging array of fraud attack capabilities on the digital identities of consumers and businesses.
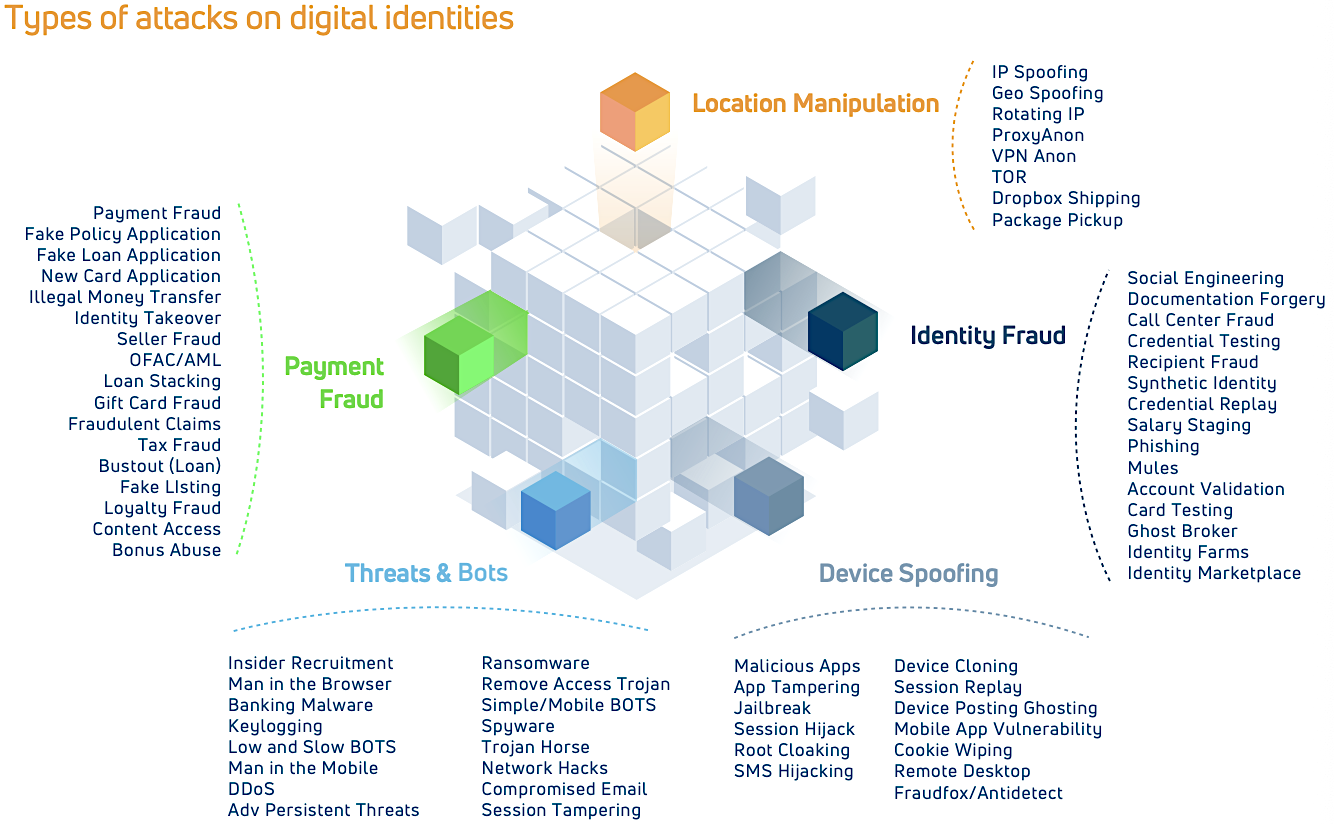
While the digital payment world has been a bit behind the curve compared to the rest of our digitised lives, it has finally gained popularity once consumers embraced their mobile devices and social media. This has led European payment card issuers and PSPs to navigate a fraud landscape never before seen. In fact, the implementation of EMV Chip and PIN was just a starting point that changed the whole game.
As we look at new fraud trends, consumers, merchants, banks, payment service providers, and processors all face an incredible array of fraud cases. Here are some of the most popular ones:
- Phishing/Pharming/Spoofing: Criminals attempt to acquire sensitive information such as usernames, passwords and credit card credentials by pretending to be a trustworthy entity in electronic communication or redirecting users to a simulated website.
- Threats/Bots: Including Malware (Ransomware and Viruses), Remote Access Trojans (RATs), Man-in-the-Middle attacks, and automated bot attacks, these are often used in combination to perform mass identity testing attacks and then take over a trusted user account.
- Fraudulent account opening/takeover: A fraudster uses stolen login details to purchase from a legitimate user’s account.
- Chargeback: typically, a user with stolen payment details purchases goods and then fraudulently attempt to secure a refund using the chargeback process.
- High-tech data breach: A specialised fraudster team hacks into a retailer or bank using a Trojan horse-type virus to steal thousands of valid card credentials and other payment data. This data is then sold to other criminals.
- Online purchases with stolen cards: Fraudsters will buy large volumes of products from online merchants using fraudulently obtained card information.
- Fake online shops: Fraudulently purchased products are offered to online buyers on internet auction websites or in fraudulent online shops which act as receivers of fraudulently purchased goods.
- Device Spoofing: Used to evade device recognition and detection capabilities by allowing a fraudster to masquerade as a legitimate customer, manipulate login sessions, open fraudulent accounts, intercept user credentials, or take advantage of multiple new account bonuses.
- Contactless: Fraudsters can trigger payments over a longer distance with strong reader antennas, say from outside someone’s handbag on the street.
Sign Up for Our Newsletter
Unlock updates, insights, and exclusive content delivered to you.
The Future of Fraud
EMV implementation and 3D-Secure, particularly when combined with Strong Customer Authentication, have already done their fair share in reducing fraud. In June 2021, the EBA published a report on the progress of SCA roll-out throughout the EU. The report showed significant improvement amongst issuing PSPs, resulting in a sharp decrease in fraud rates - excellent news.
Of course, card-fraud losses can only be examined in the specific context of card-use in each country. Because Okay is a Norwegian company, we have often mentioned how the Nordics constitute the most advanced and digital-ready payment markets in Europe. While there are slight variations between countries, here in Norway, BankID is used as a collaboration between Norwegian banks to increase online security for consumers and maintain a high level of protection.
An electronic identity (e-ID) scheme like BankID is the digital counterpart to a physical identification method such as a passport, ID card, or driver’s license. It gives users a digital online identity recognized by the most secure authorities in the country. This solution, jointly initiated by a group of banks, has taken a reigning position for a reason: banks that collaborate have an advantage over governmental and third-party solutions, as they have a pre-authenticated client base. Nordic banks see their e-ID schemes as an enabler for their businesses and as a product from which many other services can profit, including online merchants, payment businesses and next-generation fraud and risk prevention services.
While it would be easy for us to recommend going out and obtaining a BankID to reduce the risk of becoming a victim of fraud, the Nordic Region is, unfortunately, representing the minority and not the majority of banking services. Until eIDs become a more widespread and integrated form of identity authentication and verification, there are a few other ways to reduce the chances of becoming a victim of fraud:
- Always install the latest updates for operating systems, software, and applications, including your smartphone.
- Make sure antivirus and anti-malware solutions are automatically updated and run regular scans.
- Back up data regularly and then secure those backups.
- Be wary of scams and think twice about sharing your personal information.
- Consider getting a password manager to maintain stronger and more varied passwords.
- Avoid public wifi networks when logging into apps that require sensitive information.
- If a business or organization, create a continuity plan in case you’re the victim of a malware attack.
Ultimately, cybercriminals will always find new ways to bypass security techniques. As such, even the most robust security measures should be supported by intelligent omnichannel fraud prevention services that can learn, adapt, and quickly respond to changing fraud threats.
—————
This is the third part of a four-part series reviewing some of the basics of SCA. The first part of our Back to Basics series covers PSD2. The second covers the origins of SCA. Tune in next week for the final post, where we cover embedded finance and BaaS.
*figures are estimates - statistics vary based on year, country and geography.
Source, incl. photo: https://www.paymentscardsandmobile.com/research/european-fraud-report-payments-industry-challenges/